-
United States (EN)
Global
-
Africa
-
Asia Pacific
-
Europe
-
Latin America
-
Middle East
-
North America
- |
- BUSINESSES
- |
- Contact
- |
-
United States (EN)
Global
-
Africa
-
Asia Pacific
-
Europe
-
Latin America
-
Middle East
-
North America
- |
- BUSINESSES
- |
- Contact
- |
You are browsing the product catalog for
You are viewing the overview and resources for
- News
- What is Malware?
It’s no secret that our computers, phones, and other devices, contain much of our lives: from irreplaceable photos and important files to banking information or even health and personal data.
On an individual level, if our devices get infected with malicious software – malware for short – those valuable contents can get stolen, deleted, leaked or corrupted. Cybersecurity attacks can pose even more dangerous – and costly – consequences for businesses and organizations, ranging from lawsuits and crisis communications to business disruptions and privacy leaks – and beyond.
But how exactly do malware attacks happen? And what can we do to protect our devices? Here’s what you need to know.
Software vs. malware: What’s the difference?
Software or code is typically developed to do something productive, faster, and more efficient than methods before. Maybe it’s a word-processing, photo storage, or another program that is meant to do something good.
Cybercriminals write software code that does the opposite: something unintended or malicious. Malware can give cybercriminals access to and the ability to steal information, which seems bad enough as is – but today, malware poses even more severe threats to technology.
According to Donovan Tindill, senior cybersecurity strategist and expert in industrial control systems (ICS) infrastructure and operational technology (OT) cybersecurity, this is because malware continues to get more advanced over time.
“As people become more dependent on their devices, malware becomes more disruptive,” Tindill said.
Today, one of the biggest threats is that malware can cause what are known as cyber-physical or kinetic consequences when targeting ICS and OT. Historically, malware would result in information loss, unauthorized use, or denial of access – but many sectors rely on computers to operate machines, pumps, motors, and more.
“This is where we are trending: with increased digital transformation and connectivity, this is being leveraged by attackers to control someone’s computer or physical assets, like warehouses, pipelines and water treatment,” Tindill said.
Types of Malware:
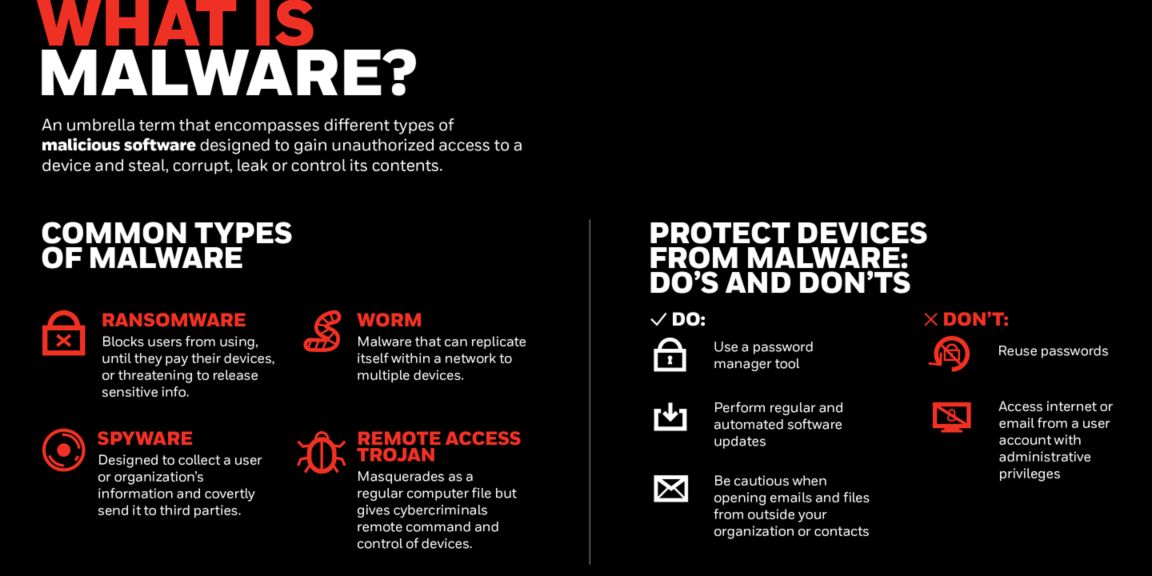
Malware is an umbrella term that encompasses different types of malicious software. Here are some of the common methods of malware:
- Ransomware: an increasingly dominant cyberthreat. Groups behind ransomware attacks benefit financially from the campaigns – which block users from using their devices, or threatening to release sensitive info, until they pay. Even when they pay, their files or the integrity of their devices may no longer be trustworthy.
- Spyware: malware that is designed to collect a user or organization’s information and covertly send it to third parties.
- Worm: malware that can replicate itself within a network to multiple devices.
- Remote Access Trojan: a type of malware designed to masquerade as a regular computer file, but unknowingly gives cybercriminals remote command and control their device.
How can a device get infected with malware?
Using USBs and removable media devices is a common source of malware attacks.
According to our 2021 USB Threat Report, which analyzed data from hundreds of energy, oil and gas, chemical, buildings, aerospace and other industrial plants, 37% of cybersecurity threats were specifically designed to utilize removable media devices – up from 19% in the 2020 report and 9% in the 2019 report.
“The flaw today is that when you plug a USB device into your computer, it trusts it automatically,” Tindill said.
Malware attacks also commonly stem from phishing emails – emails that leverage social engineering to entice the recipient to open its attachments or click its links. The messages lead to downloading different malware listed above and allow cybercriminals to obtain information or unauthorized access.
Malicious emails continue to pose by-far the biggest threat today, Tindill said.
What can we do about malware?
There are steps we can take to protect our devices from malicious software, including: avoiding accessing Internet or email with a user account that has administrative privileges, being cautious when opening emails or files from outside your contacts list or organization, never reusing passwords (and instead, using a password manager tool), performing regular and automated software updates and leveraging browser plugins that help filter malicious content.
But Tindill said that more and more, people should take a zero-trust approach to their devices – in other words: “trust nothing” and “always verify.”
“Over the years, a lot of our code has assumed trust, such as correct user input or no remote access” Tindill said. “Zero trust is the most recent paradigm shift that we trust what’s in our computers less and less because what’s hiding behind could be malware.”
For businesses undergoing a digital transformation journey, adopting a zero-trust approach to cybersecurity today will have cost savings in the future.
“If you’re transforming, you’re upgrading or implementing new digital systems and improving the performance of a refinery, of buildings, of airplanes and more. Cybersecurity is intended to protect this investment in technology. At the same time, from a cybercriminal’s perspective, the attack surface is bigger as we adopt new technologies. It is more cost-effective to address cybersecurity during design and implementation, rather than rework and remediate cyber risk on a live production system.”
Learn more about how you can protect yourself and your business from cyberattacks.
Copyright © 2025 Honeywell International Inc.